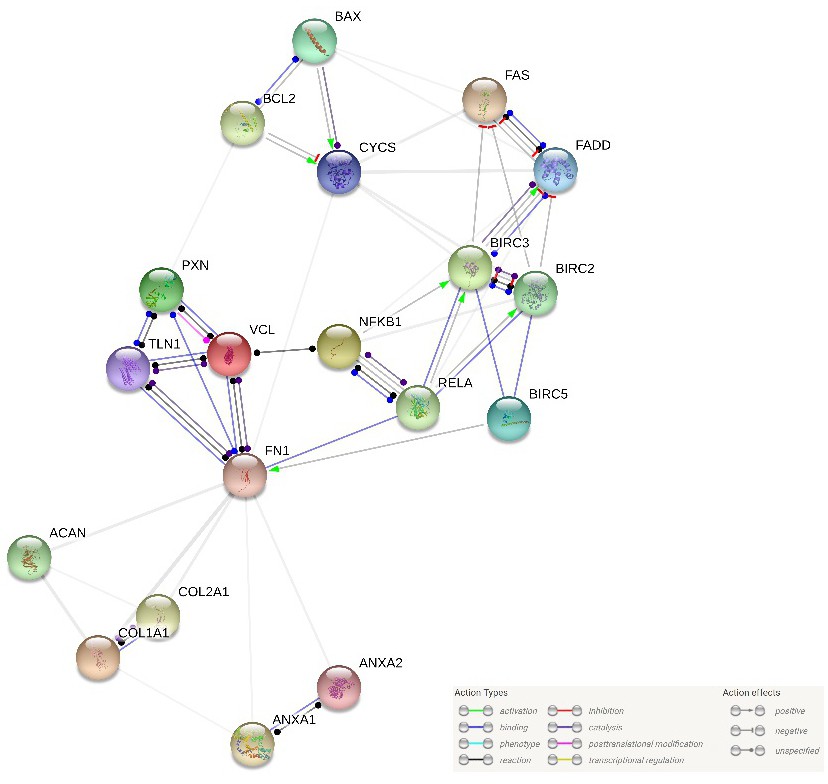
Bset osehrfof asgisvn tsucnoca isnreett rsate presents a fascinating challenge. This seemingly random string invites exploration into its underlying structure, potential meanings, and related concepts. We will delve into frequency analysis, explore potential cryptographic interpretations, and investigate visual representations to unravel the mysteries hidden within this enigmatic sequence of characters. The journey will involve examining character distributions, exploring potential patterns and algorithms, and considering various string manipulation techniques to uncover potential insights.
Our investigation will cover several key areas. First, we’ll perform a detailed analysis of character frequency and distribution within the string. This will involve creating visual representations, such as tables and graphs, to highlight patterns and anomalies. Next, we’ll explore potential interpretations, considering the possibility of codes, ciphers, or linguistic structures. We will then examine related concepts and fields, seeking connections and contexts that might shed light on the string’s origins and purpose. Finally, we will generate similar strings using various methods, comparing their properties to the original string to gain further understanding.
Generating Alternative Strings
Generating similar strings with comparable properties involves employing various techniques depending on the desired level of similarity and the properties to be preserved. These techniques range from simple character substitutions to more complex algorithms that consider phonetic similarity, semantic meaning, or even grammatical structure. The choice of method depends heavily on the application and the nature of the original string.
String Generation Methods and Examples
A straightforward method for generating similar strings is to introduce random variations within the original string. This could involve replacing characters with similar-looking ones (e.g., replacing ‘o’ with ‘0’), inserting or deleting characters, or transposing adjacent characters. For example, consider the original string “example”. We could generate alternatives such as “examp1e” (replacing ‘l’ with ‘1’), “exampl3” (replacing ‘e’ with ‘3’), or “eaxmple” (transposing ‘a’ and ‘x’). These variations maintain a high degree of visual similarity but introduce minor differences. More sophisticated methods might involve using phonetic algorithms to generate strings that sound similar, or employing natural language processing techniques to generate semantically related strings. For instance, synonyms could be substituted for certain words within a phrase to generate alternative strings conveying a similar meaning.
Comparison of Original and Generated Strings
The differences between the original string and its generated alternatives will depend on the method employed. Simple character substitution or transposition methods produce strings that are visually similar but may differ in meaning. More complex methods, such as those incorporating semantic analysis, will strive to preserve meaning while generating variations in phrasing or word choice. Similarities will include length, overall structure (for sentences or phrases), and, depending on the method, phonetic or semantic properties. For example, if the original string was a name, a generated string might preserve the initial letter or the overall sound while introducing variations in spelling or character choice.
Table of Generated Strings
| Original String | Generated String | Generation Method | Key Characteristics |
|---|---|---|---|
| example | examp1e | Character Substitution (l -> 1) | Numeral substitution, visually similar |
| example | eaxmple | Character Transposition | Slight alteration in letter order, visually similar |
| example | ExAmpLe | Case Variation | Changes in capitalization, visually similar |
| quick brown fox | rapid brown fox | Synonym Substitution | Semantic similarity, change in adjective |
Closing Summary
Through rigorous analysis and creative exploration, we’ve attempted to decipher the enigmatic string, “bset osehrfof asgisvn tsucnoca isnreett rsate.” While definitive conclusions remain elusive, our investigation has highlighted the potential for multiple interpretations and the richness of analytical approaches. The journey has underscored the intricate relationship between seemingly random sequences and the underlying structures that may govern them. The methods employed – from frequency analysis to visual representations and the generation of similar strings – offer a versatile toolkit for approaching similar challenges in the future. Further investigation, perhaps involving additional contextual information, may be needed to fully understand this intriguing string’s purpose and meaning.